Smart Lock or Spyware? The eGeeTouch TSA Travel Lock is a bit of both
In a previous post I discussed the Bluetooth pairing issue that means anyone with a sniffer and access to your lock can open it. However, this is not the most concerning aspect of the device. I’m a big fan of static analysis tools, and use a few when investigating IoT devices; they generally provide useful starting points for further investigation, and so it proved here. In this instance, MobSF produced a report that pointed at a couple of insecure Firebase databases (I’ve redacted some of the information below to casual readers from investigating further; of course, it is perfectly possible to recreate exactly what I have done. I have tried reaching out to the manufacturer on a number of occasions regarding this and the Bluetooth issue but have had no response).
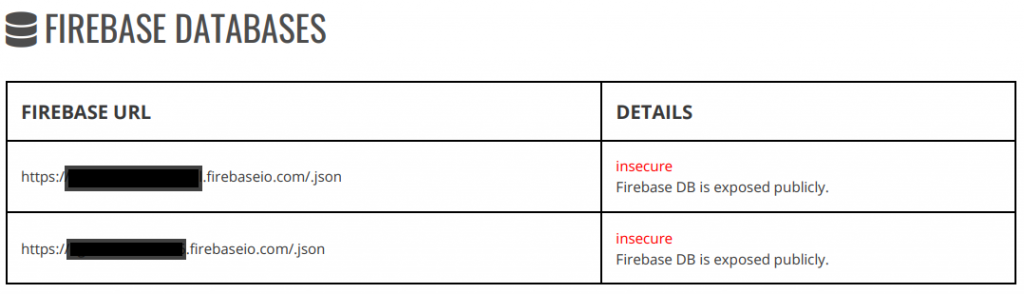
Digging down into the data returned from the URL, I had the (mis)fortune of finding my own details, captured as I tested the lock (redacted, although of course the above applies).

The information captured includes the GPS coordinates and approximate address of where the lock was accessed, the time of access, the email address of the user, and whether the device was locked or unlocked. Nowhere in the EULA is it stated that this information will be collected. Aside from why this information is stored at all (I’m assuming some sort of audit trail), it is clear that this represents a severe privacy intrusion. Not only is the device collecting personally identifiable information (PII) about the user, but it is storing it in a location that can be accessed without requiring any authentication. PII, of course, is subject to GDPR regulation in the UK and other, similar restrictions elsewhere in the world. This would seem to be, then, a significant concern for anyone tempted to buy the lock.